Azure Security Part 1: Understanding the Foundations of Azure Security Services
What does Azure provide for Security?
Microsoft Azure has a wide range of services built into their cloud ecosystem. These services provide the ability to monitor resources, create and set policies, and identify and mitigate threats within not only the Azure infrastructure, but also to external resources for a consistent security posture across an organization. In this first of a series of three articles on Azure Security, we will focus on the services that make up the foundation of an organization’s security program.
Building the Security “House”
When developing your organization’s technology platform, security should be built into the foundation. Just as the foundation of your home is stronger and more protected built with bricks and mortar instead of straw and sticks, the same should be true with security for your technology “house”.
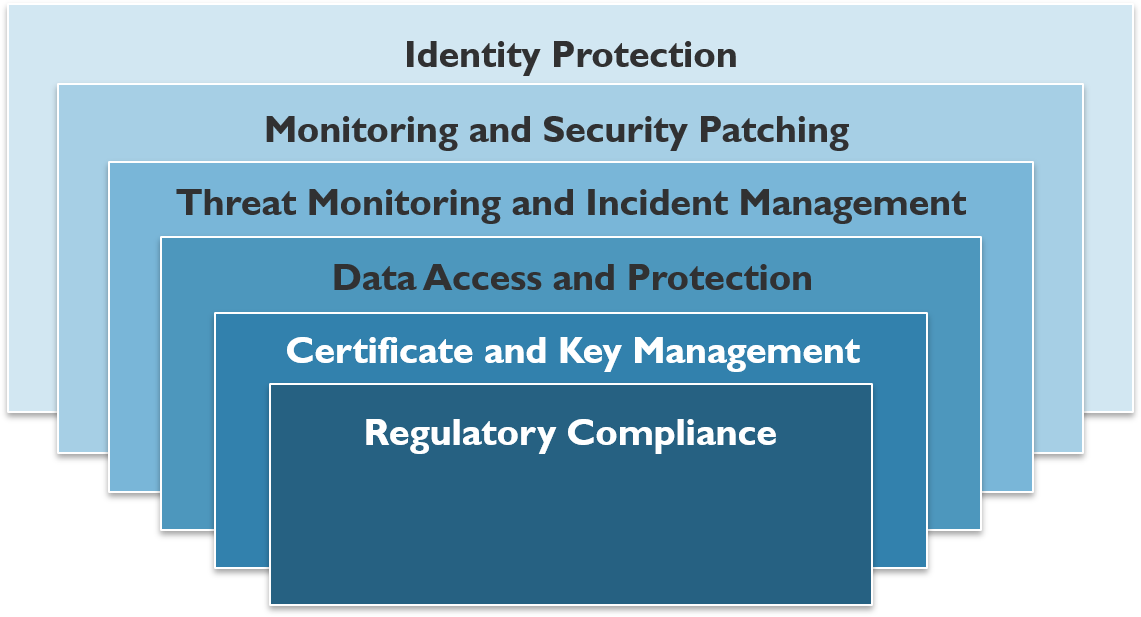
It is important that you determine a proper foundational plan for security at the very beginning, before you start building out an infrastructure. This would include areas such as:
Identity protection
Monitoring and security patching
Threat monitoring and incident management
Data access and protection
Certificate and key management
Regulatory compliance
These services together help to provide security Defense in Depth. No one service is going to provide the level of security needed for an enterprise but layering many of these services together creates a secure program for the organization. The list here is in no way all inclusive, but it does line up well with services that are available within Azure.
This article will focus on four key areas that could be viewed as the foundation of security services within Azure:
Identity Protection
Monitoring and Patching
Data Protection
Security Center
Additional articles in this series will provide more information on Security Policies for security best practices and regulatory compliance, and Security Alerts and Playbooks for threat monitoring and incident management. Microsoft also provides information on their security services here: https://azure.microsoft.com/en-us/overview/security/
Identity Protection
The most important resource in any organization is its people, and the safety of those people should always be the number one priority. This includes physical safety as well as protection of their personal identifiable information (PII). The foundation of accomplishing this within the Azure ecosystem is within Azure Active Directory (Azure AD).
Azure AD provides a single platform to manage organization users, groups, and resource roles and access. In addition, Azure AD Privileged Identity Management provides an added level of security and management for administrative roles within the organization. It is important to understand that within the Azure (and Microsoft 365) subscription, Azure AD is included and allows users and groups to be created and given Role-based Access (RBAC) to resources at no additional charge. Azure AD Connect can be used to synchronize on-premises Active Directory domains to Azure Active Directory in order to maintain access to on-premises and cloud resources. Beyond RBAC capabilities within Azure AD, additional services can be configured to protect data assets through Multi-factor Authentication (MFA) and Conditional Access Policies.
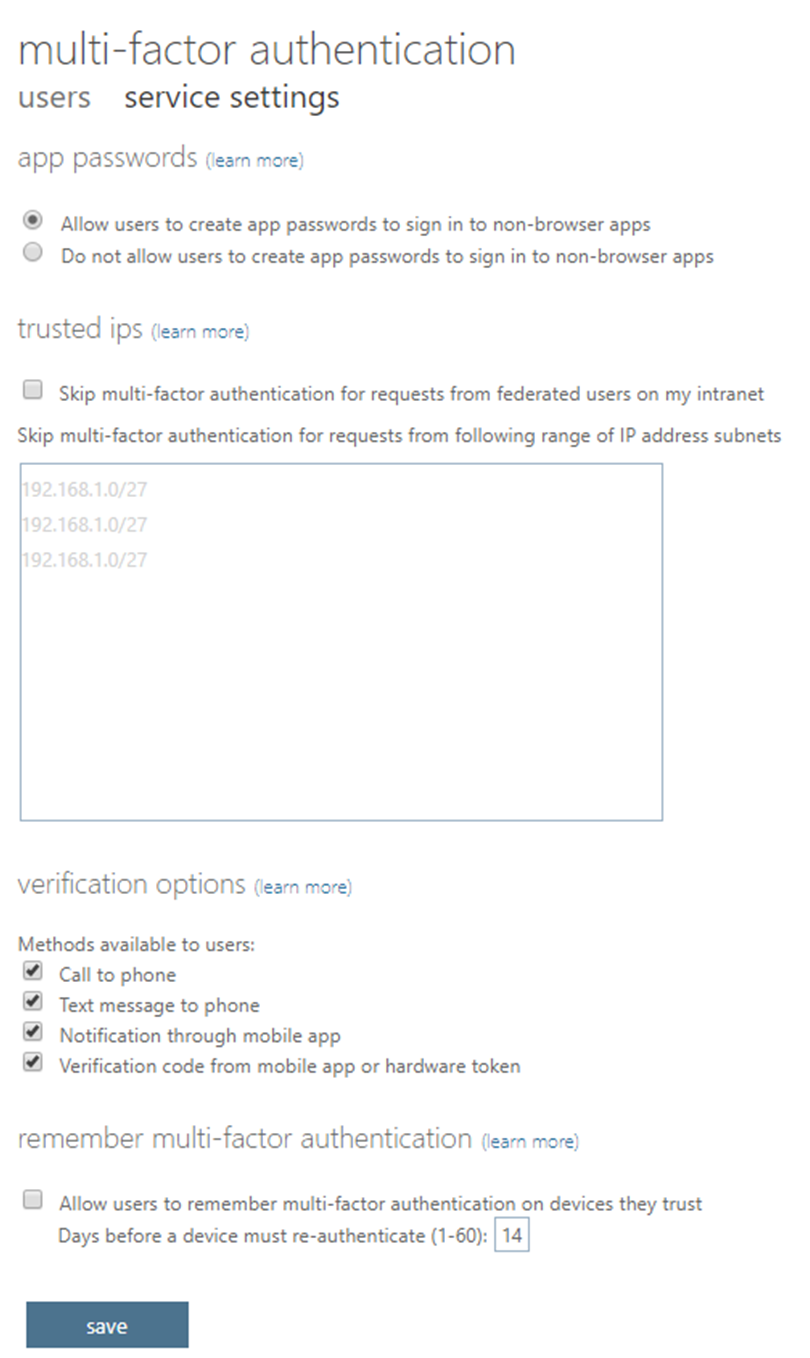
MFA, when enabled, requires a user to provide more than a single means to identify that they are who they say they are. Typically, you have a password that is associated to a username or email address to login to an application, device, or website. Utilizing MFA will require a second piece of information for proof, such as a phone app or a code texted to your cell phone. This protects the organization from a breach if passwords become compromised. It is much less likely that an attacker will be able to learn a password AND gain access to a user’s phone together. MFA has the capability to be assigned and enforced to individual users or groups. Conditional Access Policies and Privileged Identity Management (PIM) provide additional customization to the enforcement of MFA and access to resources.
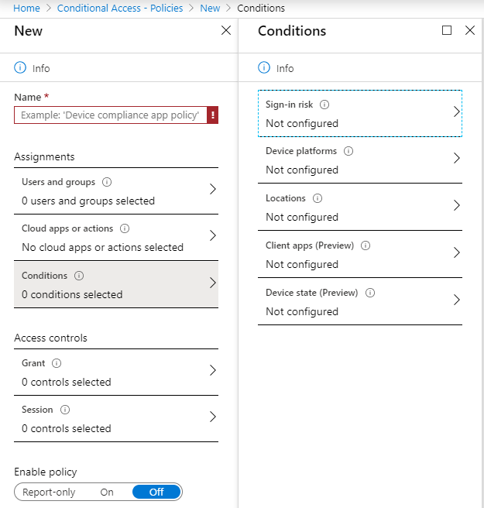
Conditional Access Policies provide a level of security that can enforce additional authentication or block access completely based on set requirements that include sign-in locations, device platform, device state, or client applications. These conditions can be assigned to specific users or groups, and if these conditions are in place, access can be set to require MFA or blocked completely. Conditional Access Policies can protect organizations from data breaches from access on suspect devices, IP addresses, or applications. Conditional Access Policies require an Azure Active Directory Premium P1 license.
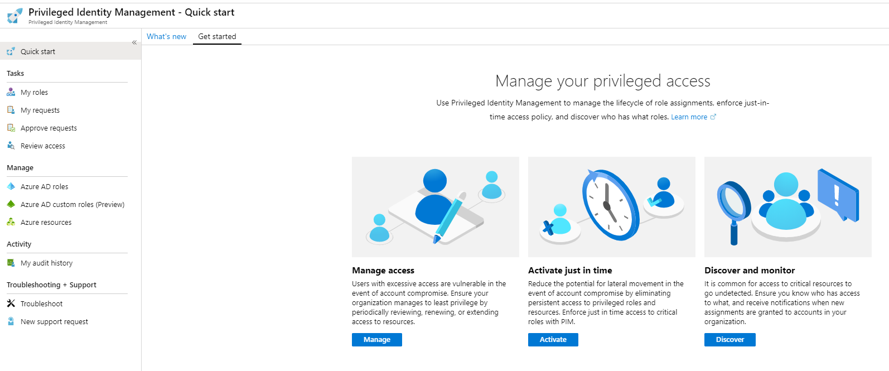
PIM requires additional licensing but allows for temporary assignment of administrative privileges to users that may not require them all the time. This service also provides a level of audit reporting on who has administrative rights for increased monitoring and management. Privileged Identity Management requires an upgraded license to Azure AD Premium P2.
Monitoring and Patching
Monitoring and Patching are fundamentally important even though sometimes overlooked by organizations. Maintaining updated patches on infrastructure and endpoints provide a consistent baseline of security within the environment. Azure Monitor has built in services to deploy agent extensions to both Azure virtual machines and external servers that can be monitored through the same dashboard. Azure Monitor can be configured with alerts based on update activities such as installation, cancellation, or simply assess available patches. Actions can then be created on what should be done when an activity alert is triggered.
Data Protection
Data is at the heart of everything within an organization. Data includes financial information, customer information, intellectual property, personnel information, etc. A loss of data would be disastrous to any organization.
With organizations relying on digital forms of data over hard copies, the protection of this data within the cloud ecosystem is very important. Azure provides certain best practice standards for the various data that resides within their infrastructure. This includes encryption at rest for all storage accounts, default encrypted web access through HTTPS (can be user configured to allow unencrypted HTTP), and network security rules are initially set to block all in-bound connections. SQL databases have encryption settings at both application and database levels, and an additional Advanced Data Security service that will provide Advanced Threat Protection for SQL. Azure Backups and Data Life Cycle Management can be added to storage and SQL accounts for additional data protection and retention against loss.
Azure Security Center
Identity and Access (IAM), virtual machine (VM) monitoring, and data protection security best practices are all part of the Azure Security Center dashboard. Within the Azure portal, search to locate Security Center and select. When you enter Azure Security Center, the overview is displayed as a dashboard that includes the secure score, resource security hygiene, and threat protection within the currently selected directory. Each of the tiles within the dashboard allow you to select and find out more information about each. For example, you can review your secure score under policy &compliance to determine which areas may need your attention and what best practice violations have the most impact on your score. From here, you can do your own risk assessment on whether any of these findings will negatively affect your organization.
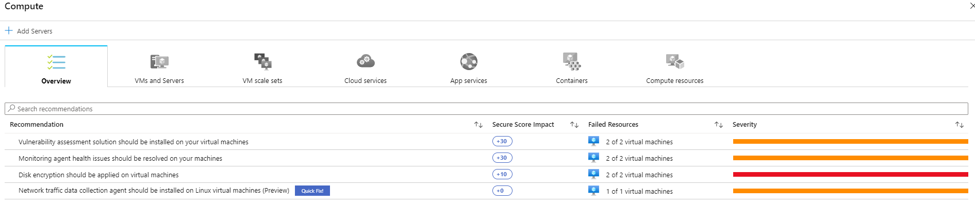
The Resource security hygiene area is helpful to understand the level of severity based on recommendations and allows you to review them based on Compute, Data, Identity, and Networking resources. Within the Compute area, you will find the recommendations for VMs, app services, containers, and other compute resources within the environment. This section will also show if the Azure Monitor agent is not installed on an Azure virtual machine. For external compute resources, if the agent is not installed, Azure Security Center would not know that it is a part of the infrastructure to provide a recommendation. Some of the recommendations may also include a “quick fix” box where you can deploy the changes directly from Security Center.
The features and functionality that has been described here is all available under the Free Tier of Azure Security Center, which makes it a very powerful tool. Upgrading to Standard Tier provides additional functionality that includes just in time VM access, adaptive application controls and network hardening, regulatory compliance dashboard and reports, and Threat protection for Azure VMs, non-Azure servers, and PaaS Services. Standard Tier pricing for virtual machines is priced at around $15 per month per VM.
What’s Next?
As you continue to build your Azure infrastructure, continue to review Azure Security Center and follow their recommendations for best practices, if possible. There are reasons why they build these services into the environment, and you should take full advantage of this powerful tool. In our next blog (part 2 of this series), we will provide some detail regarding using Azure Security Policies. What are Security Policies? Who should use them? How can they help me manage Azure resources and cost?
Other Useful Resources
1. Azure Security Center overview: https://azure.microsoft.com/en-us/services/security-center/
2. Azure Security Center price comparison: https://azure.microsoft.com/en-us/pricing/details/security-center/
3. Azure Security Center documentation: https://docs.microsoft.com/en-us/azure/security-center/
—Dwayne Natwick
Let us know about your success! We love to empower our students and promote them. You can reach us on Twitter, LinkedIn or Facebook