Azure Security Part 3: Security Center Alerts and Automation workflows
Microsoft Azure has a wide range of services built into their cloud ecosystem. These services provide the ability to monitor resources, create and set policies, and identify and mitigate threats within not only the Azure infrastructure, but also to external resources for a consistent security posture across an organization. In the first post of a series of three articles on Azure Security, we focused on the services that make up the foundation of an organization’s security program. Our second article provided guidance on how to use Policies and Initiatives to govern our Azure environment. In this, our third article, we will discuss how we can manage our environment through Security Center with the use of alerts and automation workflows.
How can Azure Security Center be used for management?
Azure Security Center provides a central source for gathering information from through your Azure environment and reviewing that information based on security best practices. Security Center presents that information in various ways that allow you to evaluate the resources and controls within your environment for potential vulnerabilities and threats. The information can be presented at the resource level, threat level, and regulatory compliance level. The amount of information provided is extremely helpful to understand how enabling a control will increase your level of security within the environment in comparison to industry best practices. The information and recommendations presented in Security Center helps you to manage how resources are deployed and protected on an on-going basis.
Of course, the information within Azure Security Center is only useful if someone is reviewing it and acting upon the recommendations provided. What happens if no one is reviewing Security Center? How is the review, response, and remediation handled by your organization? What happens if a new threat presents itself to your environment and no one is watching the threat protection dashboard?
Security Center has a way to address this with workflow automation. Workflow automation works similar to Alerts and Actions within Azure Monitor, but there are differences in how it is setup. The following sections will walk you through the components of a Security Center automation workflow, and the steps that you would take to create them within Security Center.
What are the components of the workflow?
Security Center workflow automation allows you to create a trigger and from that trigger, initiate an action. These workflows are created at the subscription level, and you are able to have multiple workflows to cover multiple triggers. Let’s talk about the main components to creating a workflow.
Trigger conditions
The trigger conditions are the alert criteria that initiates an action. Trigger conditions have two data types within Security Center that can be used, Threat detection alerts and Security Center recommendations.
These data types can be thought of in the sense of active alerts and passive alerts. Threat detection alerts would be active and based on potentially an event that could immediately impact the security of your environment. These alerts should be responded to right away. Security Center recommendations can be thought of as passive. Recommendations are just that, and they should be reviewed for potential impact, but unlike the detection of a threat, these recommendations may not be something that are an active exploit to your environment. These alerts can make you aware of a newly deployed resource that is out of compliance to a policy, however.
After you have determined the data type that will be used for the trigger condition, you can then identify the details that will initiate an action to take place. This can get as defined as a specific Security Center recommendation or a threat alert name. The final criteria is the severity or state of the condition. Severity can be low, medium, and/or high, and state, which only pertains to recommendation triggers, is unhealthy, healthy, and/or not applicable. These can be selected in an individual, multiple, or all selection. Best practice would be to select the high severity and unhealthy state, at a minimum.
Logic Apps
Once a trigger condition is met, an action needs to take place based on the trigger conditions. This is where Logic Apps come into play. Security Center workflow automation was compared to Monitor alerts and actions earlier in the article. Where they differ is that where Monitor has the ability to define the condition, action groups, and alert within configuration tile, Security Center workflow automation requires a Logic App to be used to configure the action and alert that will take place once the trigger conditions are met.
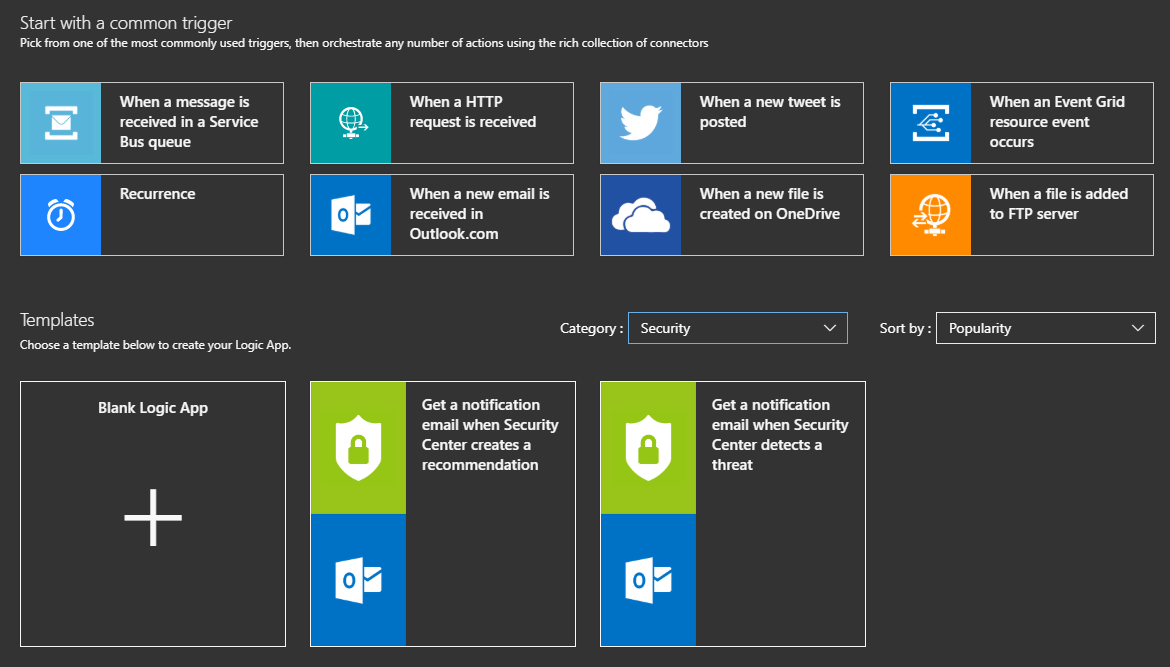
The Logic Apps Designer is used to configure these actions and alerts. For Azure Security Center, there are two templates available that are built for the trigger conditions in Security Center workflow automation. These can be located easily within the templates by filtering on the Security category.
Logic App Designer follows a logical if this happens, then do that approach. The available templates simply get a notification that the trigger condition has been met, and send a notification email to addresses or distribution lists that you identify. These templates do allow for additional actions to be added, if needed.
Detail of workflow automation creation steps
Here are the steps and order of operations for creating a workflow automation within Security Center. The first step when creating a workflow automation is to create a Logic App that will be used as the alert/action for the workflow. If you already know whether the workflow trigger data source is going to be a threat detection alert or a Security Center recommendation, then you can create a single Logic App within the designer. If you plan to create workflows for both data sources, then you can just create two Logic Apps.
To create a Logic App:
Navigate to Logic App within the Azure Portal
Select +Add for a new Logic App
Select the subscription
Select or create a Resource Group
Enter a name
Select the region Location
Select Review + Create, and then Create
Upon create, you will be taken to the Logic App Designer
Under the Templates section, under Categories, select Security (see screen shot in Logic App section of this article
Two templates will be available based on which trigger data source you will use
Select one of these templates and follow the steps to configure. This will include connecting your O365 account, connecting to Security Center, and configuring the notification email addresses and message.
Save the designer when complete
To create a Workflow:
Navigate to Security Center
In the menu, select Workflow automation
Select +Add Workflow automation
Enter a Name for your workflow
Select a Resource group
Configure the Trigger conditions
Under Actions, select the Logic App that you created
Select Create
Once the deployment is complete, the Workflow automation will be visible in the table with a Status of enabled. If you need additional workflow automations, follow the same steps and the list will continue to be populated in the table.
Azure Security Center
Azure Security Center is a central source for the overall security health of your organization’s environment. The tools that are available not only provide visibility into your security posture versus best practice controls, but also assist in managing potential active threats to your environment. Workflow automation addresses the need to know these vulnerabilities and threats actively to respond and remediate any potential issues before they become a wide-scale issue
What’s Next?
As you build your Azure infrastructure and continue to add resources, it continues to be important that you manage these resources and monitor them for vulnerabilities against the overall organizations security posture and overall best practices. Azure Security Center can help through usage of these workflow automation tools to manage security alerts and vulnerabilities in security controls.
Other Useful Resources
Azure Security Center documentation: https://docs.microsoft.com/en-us/azure/security-center/
Security Center Workflow automation documentation: https://docs.microsoft.com/en-us/azure/security-center/workflow-automation
Logic Apps documentation: https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-overview
Microsoft Learn modules on Azure Policy: https://docs.microsoft.com/en-us/learn/browse/?products=azure&term=policy
Azure policy samples: https://docs.microsoft.com/en-us/azure/governance/policy/samples/
Azure Policy overview: https://docs.microsoft.com/en-us/azure/governance/policy/overview
Built-in policies: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-policies
Built-in initiatives: https://docs.microsoft.com/en-us/azure/governance/policy/samples/built-in-initiatives
Tutorial on creating a custom policy definition: https://docs.microsoft.com/en-us/azure/governance/policy/tutorials/create-custom-policy-definition
Let us know about your success! We love to empower our students and promote them. You can reach us on Twitter, LinkedIn or Facebook