AZ900 – Networking Security
In the last post in the AZ900 series, we looked at the basic components of Azure Networking. We are now going to look at some of the security options available within Azure.
Your data and applications can be deployed with these security features to protect against unauthorized access. Microsoft uses a series of process to layer protections around their datacenters. This strategy is called defence-in-depth and can be used to slow and alert against attacks.
Network Security Groups (NSG)
In the previous post, I discussed the benefits and how to use Virtual Networks (VNets). Network Security Groups (NSGs) work alongside VNets to filter traffic to and from specific Azure resources. NSGs can contain inbound and outbound security rules to filter the traffic by IP address, port or protocol. All Network security groups contain default rules that provide a basic protection level. You can use custom rules to override the default rules, but the default rules cannot be deleted and are present in all NSGs.
These NSG rules can provide internal protection for your Azure resources by providing traffic filtering to individual network interfaces or subnets within virtual networks.
Azure Firewall
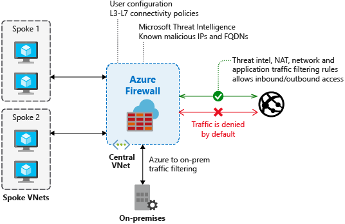
Typically deployed to a central Virtual Network (VNet) for general network access, Azure Firewall is a managed firewall service hosted in the cloud used to protect your Azure resources. The Azure firewall monitors incoming and outgoing network traffic, allowing only the traffic you wish into or out of your Azure Network. The Azure Firewall is stateful, so the full context of the network traffic is inspected rather than individual network packets.
A set of firewall rules defines network restrictions. These Firewall rules can take the form of Application rules, Network rules, and Network Address Translation (NAT) rules
Application Rules
Applications rules use fully qualified domain names (FQDNs) to define what can be accessed from subnets.
Network Rules
Network rules have source and destination addresses, ports and protocols defined.
NAT Rules
NAT rules are used to define destination IP addresses and the ports to translate inbound requests too.
The Azure Firewall service provides many different features which include:
High Availability, is built-in, removing the requirement for additional load balancers.
Scalability, the Azure Firewall can scale as much as needed to accommodate your network traffic.
Threat intelligence, Azure Firewall can alert and deny traffic from IP addresses flagged as malicious from the Microsoft Threat Intelligence feed.
Traffic filtering, rules can be created to allow or deny network traffic based on IP address, port and protocol.
Azure Monitoring, Azure Monitor is integrated with Azure Firewall events, allowing logging of activity.
DDoS Protection
Applications that are internet facing are always susceptible to distributed denial of service (DDoS) attacks. These attacks are designed to exhaust and overwhelm the application's resources, resulting in slow and unresponsive systems for users.
To prevent these types of attacks, Azure offers Azure DDoS Protection. This protection helps keep your applications running and available to valid users by analyzing and discarding malicious traffic at the end of the Azure network before it even reaches your application, whilst allowing legitimate traffic to be unaffected.
One benefit of DDoS Protection is that it prevents unnecessary scaling if your application has been configured to auto-scale resources to cope with demand. Then under a DDoS attack, your application would scale out causing additional expense.
Microsoft offers two tiers of DDoS Protection
Basic DDoS Protection
All standard Azure subscriptions automatically enable Basic DDoS Protection for free. It is designed to protect the Azure infrastructure from DDoS attacks by utilizing the same traffic monitoring and real-time protection against common network attacks used by Microsoft's own online services.
Standard DDoS Protection
The Standard tier has all the Basic protection features. It also includes protection profiling that uses machine learning to monitor your applications specific traffic over time and update the profile to best suit your service.
The Standard tier can protect against volumetric attacks, which is when the network is flooded with large amounts of traffic which seems legitimate. It also protects against protocol attacks where attackers use weaknesses in the protocol stack, to make resources inaccessible.
If deployed with a Web Application Firewall (WAF), the standard plan protects the network layer from attack and the WAF protects against application-layer attacks, providing multi-layer protection to your applications.
Microsoft also offers alerting and reporting at the Standard tier to assist your security and infrastructure teams in responding to attacks and improving your deployed systems' resilience. The Standard tier is aimed at larger enterprise customers as coverage starts at 100 resources with public IP addresses. However, a single DDoS plan can be used across multiple subscriptions in a single tenant.
Summary
So, we have looked at some of the networking options offered by Microsoft. These services can be used to provide additional defence-in-depth when combined to ensure the protection of you Azure resources.
Network Security Groups provide traffic filtering to resources within virtual networks, while an Azure Firewall is a centralized firewall providing network-level protection to your subscriptions. Used in conjunction with each other, they enhance your network-level protection.
DDoS Protection, combined with a Web Application Firewall (WAF), provided even more protection at the application layer, preventing common exploits and vulnerabilities.
— Matt Boyd